Structural models of software display the organization of a system in terms of the components that make up that system and their relationships.
We’re going to focus on class diagram for modeling the structure of the classes in a software system.
Class Diagram
We will use the information we have from the conceptual model about our objects to create the class diagram.
Naming Convention
You start by using a way for naming your classes. Usually, the class name is in the singular, and uppercase first later, like “BankAccount”.
For the attributes, and methods, they are in camel case; lower case first letter, and all other words begins with upper case letter, like “getProductDetails”.
Some people prefer to use uppercase first letter for private attributes and methods, but it doesn’t matter, unless you’re using one way for naming, and your code is clear, easy to read and maintain.
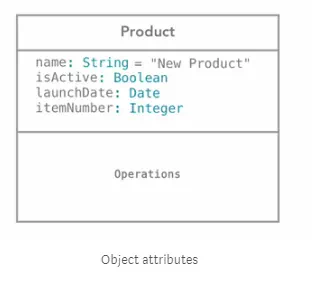
Attributes
We then write the attributes, their data types and their default value if exist.
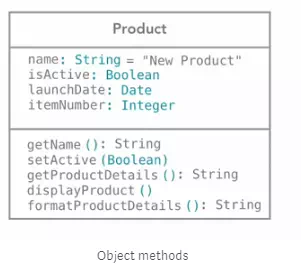
Methods
Write the methods, their parameter if exist inside a parentheses, and their return type.
Public, Private and Protected
They are called the access modifiers. They are used to control the access to object’s members.
Now, a good case practice is to keep all you members (attributes and methods) private unless it needs to be exposed.
So, we use signs to denote the access modifier of each member in the class.
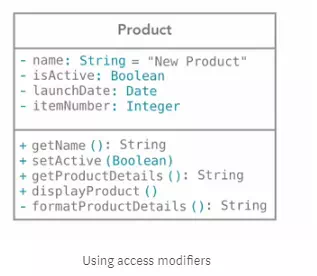
· Public (‘+’): It says that it can be seen and triggered at any part of the application
· Private (‘-’): It says that it can be only triggered inside it’s class only
· Protected (‘#’): It says that it can be only triggered inside it’s class and also inside the child classes.
Some developers tend to keep their attributes private even if they know some other class need to trigger them. They allow getting and setting the value of these attributes through what’s called Getters and Setters. These are methods to get and set the attributes without allowing any external code to have a direct effect on them.

