In the late 1960s, the US Department of Defense decides to make a large network from a multitude of small networks, all different, which begin to abound everywhere in North America. We had to find a way to these networks coexist and give them an outdoor visibility, the same for all users. Hence the name of InterNetwork (interline), abbreviated as Internet, data this network of networks.
The Internet architecture is based on a simple idea: ask all networks want to be part of carrying a single packet type, a specific format the IP protocol. In addition, this IP packet must carry an address defined with sufficient generality in order to identify each computer and terminals scattered throughout the world. This architecture is illustrated in Figure.
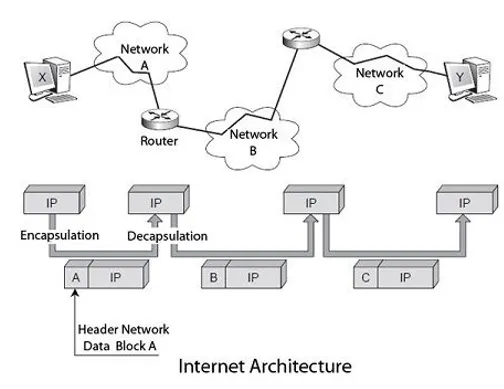
The user who wishes to make on this internetwork must store its data in IP packets that are delivered to the first network to cross. This first network encapsulates the IP packet in its own packet structure, the package A, which circulates in this form until an exit door, where it is decapsulated so as to retrieve the IP packet. The IP address is examined to locate, thanks to a routing algorithm, the next network to cross, and so on until arriving at the destination terminal.
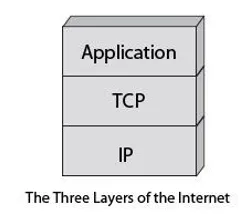
To complete the IP, the US Defense added the TCP protocol; specify the nature of the interface with the user. This protocol further determines how to transform a stream of bytes in an IP packet, while ensuring quality of transport this IP packet. Both protocols, assembled under the TCP / IP abbreviation, are in the form of a layered architecture. They correspond to the packet level and message-level reference model.
The Internet model is completed with a third layer, called the application level, which includes different protocols on which to build Internet services. Email (SMTP), the file transfer (FTP), the transfer of hypermedia pages, transfer of distributed databases (World Wide Web), etc., are some of these services. Figure shows the three layers of the Internet architecture.
IP packets are independent of each other and are individually routed in the network by interconnecting devices subnets, routers. The quality of service offered by IP is very small and offers no detection of lost or possibility of error recovery packages.
TCP combines the functionality of message-level reference model. This is a fairly complex protocol, which has many options for solving all packet loss problems in the lower levels. In particular, a lost fragment can be recovered by retransmission on the stream of bytes. TCP uses a connection-oriented mode.
The flexibility of the Internet architecture can sometimes be a default, to the extent that global optimization of the network is carried out by sub-network subnet, by a succession of local optimizations. This does not allow a homogeneous function in different subnets traversed. Another important feature of this architecture is to place the entire control system, that is to say, intelligence and control of the network, in the terminal machine leaving virtually nothing in the network, at least in the current version, IPv4, the IP protocol. The control intelligence is in the TCP software on the PC connected to the network.
It is the TCP protocol which takes care of sending more or fewer packets according to network load. Precise control window the maximum number of unacknowledged fragments that may be issued. The TCP window control increases or decreases the traffic following the time required to complete a round trip. Over this time increases, Considering the more congested network, and the transmission rate must decrease to counter saturation. In return, the infrastructure cost is extremely low; no intelligence is not in the network. The service provided by the network of networks corresponds to a quality called best effort, which means that the network does its best to carry the traffic. In other words, the service quality is not assured.
The new generation of IP, IPv6, introduces new features that make the nodes of the network smarter. The new generation of routers comes with QoS management algorithms, which allow them to provide transportation can meet time constraints or packet loss. We expect the arrival of IPv6 for ten years, but it’s still IPv4 IP that governs the world. The reason for this is that every new need achievable with IPv6, IPv4 has been able to find the algorithms needed to do as well.
In IPv4, each new customer is treated the same way as those already connected with resources being distributed equitably among all users. The resource allocation policies of telecom operator’s networks are totally different, since, on these networks, a customer who already has a certain quality of service does not suffer any penalty because of the arrival of a new customer. As discussed, the now advocated solution in the Internet environment is to encourage customers with real-time requirements, using appropriate protocols, using priority levels.
The IP protocol for thirty years, but remained almost confidential for twenty years before taking off, unless its properties as a result of the failure of the protocols directly related to the reference model, too many and often incompatible. The IP world growth comes from the simplicity of its protocol, with very few options, and it’s free.

Comments are closed.