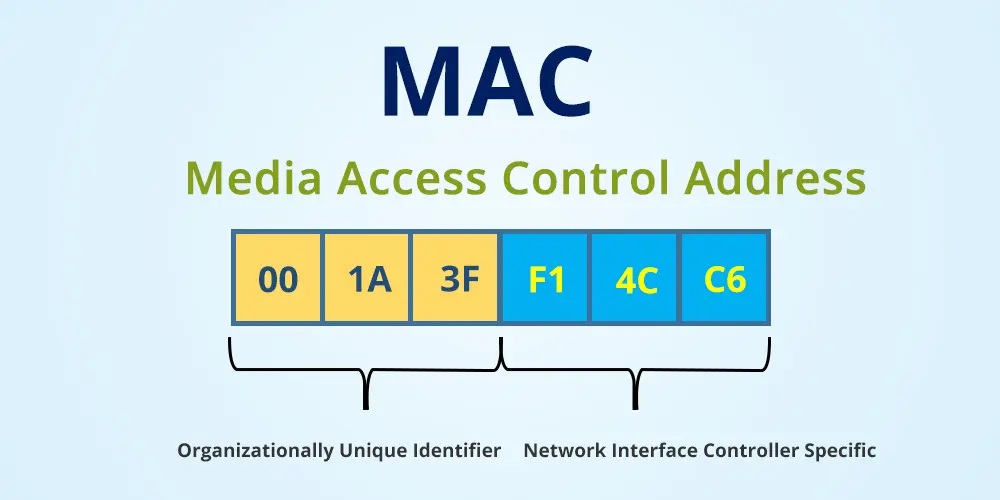
Definition: Media access control (MAC) and logical link control (LLC) are the sublayers of the data link layer (Layer 2) in OSI Reference Model. ‘MAC’ is also refer to as MAC layer. It use MAC protocols to provides unique addressing identification and channel access control mechanism for network nodes to communicate with other nodes across a shared channel.
MAC describes the process that is employed to control the basis on which devices can access the shared network. Some level of control is required to ensure the ability of all devices to access the network within a reasonable period of time, thereby resulting in acceptable access and response times.
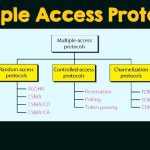
It is also important that some method exists to either detect or avoid data collisions, which are caused by multiple transmissions being placed on the shared medium simultaneously. Media Access Control can be accomplished on either a centralized or decentralized basis, and can be characterized as either deterministic or non-deterministic in nature.
Centralized Control
A centralized controller polls devises to determine when access and transmission by each station is allowed to occur. Stations transmit when requested to do so, or when a station transmission request is acknowledged and granted. This process of polling requires the passing of control packets, adding overhead and reducing the amount of throughput relative to the raw bandwidth available. Additionally, the failure of the central controller will disrupt the entire network; in such an event, the controller is taken off-line and a backup controller assumes responsibility. Centrally, controlled networks generally employ deterministic access control; Token Ring and FDDl networks are centrally controlled.
Deterministic Access
Deterministic access is a media access control convention that allows both the centralized master station and each slaved station to determine the maximum length of time which will pass before access is provided to the network. In other words, each station can be guaranteed the right to communicate within a certain time frame. Additionally, the system administrator can assign access priorities. Deterministic access is also known as noncontentious, because the devices do not contend for access, rather access is controlled on a centralized basis.
Deterministic access employs token passing. The token, which consists of a specific bit pattern, indicates the status of the network whether it is available or unavailable. The token is generated by a centralized master control station and transmitted across the network. The station in possession of the token is in control of access to the network. It may transmit or may require other stations to respond. After transmitting, the station will pass the token to a successor station in a predetermined sequence while the process is complex and overhead intensive, it yields careful control over the network.
Deterministic access is especially effective in high-traffic environments where a lack of control would cause chaos in the form of frequent data collisions.
General characteristics of token-based networks include a high level of access control, which is centralized. Access delay is measured and assured, with priority access being supported. Throughput is very close to raw bandwidth, as data collisions are avoided; throughput also improves under load, although absolute overhead is higher than is the case with non-deterministic access techniques. Deterministic access standards include Token-Passing Ring, IBM Token Ring, and Token-Passing Bus.
Token-based LAN technologies are somewhat overhead intensive, due to the token passing and management processes. However, they can more than compensate for that fact by virtue of the avoidance of data collisions. Token Ring, for instance comes in 4, 16and 20 Mbps. In each case bandwidth utilization is virtually 100%.
Non-deterministic Access
Non-deterministic media access control, places access control responsibilities on the individual stations. This is popularly known as Carrier Sense Multiple Access (CSMA), and is most effective in low-traffic environments. There are two variations, CSMA/CD and CSMA/CA.
CSMA is a decentralized, contentious media access control method used in Ethernet and other bus oriented LANs. Each of multiple stations, or nodes, must sense the carrier to determine network availability before access to the medium to transmit data: further, each station must monitor the network to determine if a collision has occurred. Collisions render the transmission invalid and require retransmission. In the event of a busy condition, the station will back off the network for a calculated random time interval before attempting subsequent access.
CSMA is implemented in two standard means, CSMA/CD and CSMA/CA. In either case, latency and throughput degrade under heavy loads of traffic. For example, an Ethernet network running at a theoretical speed of 10Mbps typically provides about 4 to 6 Mbps throughput. While it is less costly than Token Ring networking, it also delivers less efficient use of bandwidth.
Carrier Sense Multiple Access with Collision Detection (CSMA/CD).This is the most common media access control method used in bus networks. At that point, all devices back off the network, calculating. a random time interval before attempting a retransmission .
Carrier Sense Multiple Access/Collision Avoid (CSMA/CA). This includes a priority scheme to guarantee the transmission privileges of high-priority stations. CSMA/CA requires a delay in network activity after each transmission is completed. That delay is proportionate to the priority level of each device, with high-priority nodes programmed for short delays and with low-priority nodes programmed for relatively long delays. As collisions may still occur, they are managed either through Collision Detect or through retransmission after receipt of a Negative Acknowledgment (NAK). CSMA/CA is more expensive to implement, as it requires that additional programmed logic be embedded in each device or NIC. CSMA/CA does, however, offer the advantage of improved access control, which serves to reduce collisions and, thereby, improve the overall performance of the network.